AWS SAML database access via Okta
Note: This feature is available in Enterprise, AWS, Team editions only.
Table of contents
Overview
CloudBeaver allows for database connections through AWS SAML with Okta authentication. This guide details the process for establishing such connections. Please ensure you meet all the prerequisites outlined below before proceeding with the configuration steps.
Prerequisites
- AWS IAM Configuration: An active configuration of AWS IAM is necessary. This includes a properly set up AWS account with IAM Connect enabled. Additionally, ensure the account has the required permissions to create and manage identity providers and roles.
- Okta setup: Access an Okta account with the necessary permissions to configure applications.
- CloudBeaver administrative access: Ensure administrative privileges in CloudBeaver.
For this type of authentication, proxy access keys and secret keys are not required. This means there is no need to generate static keys in AWS.
Configuration Steps
Log in to CloudBeaver as an Administrator.
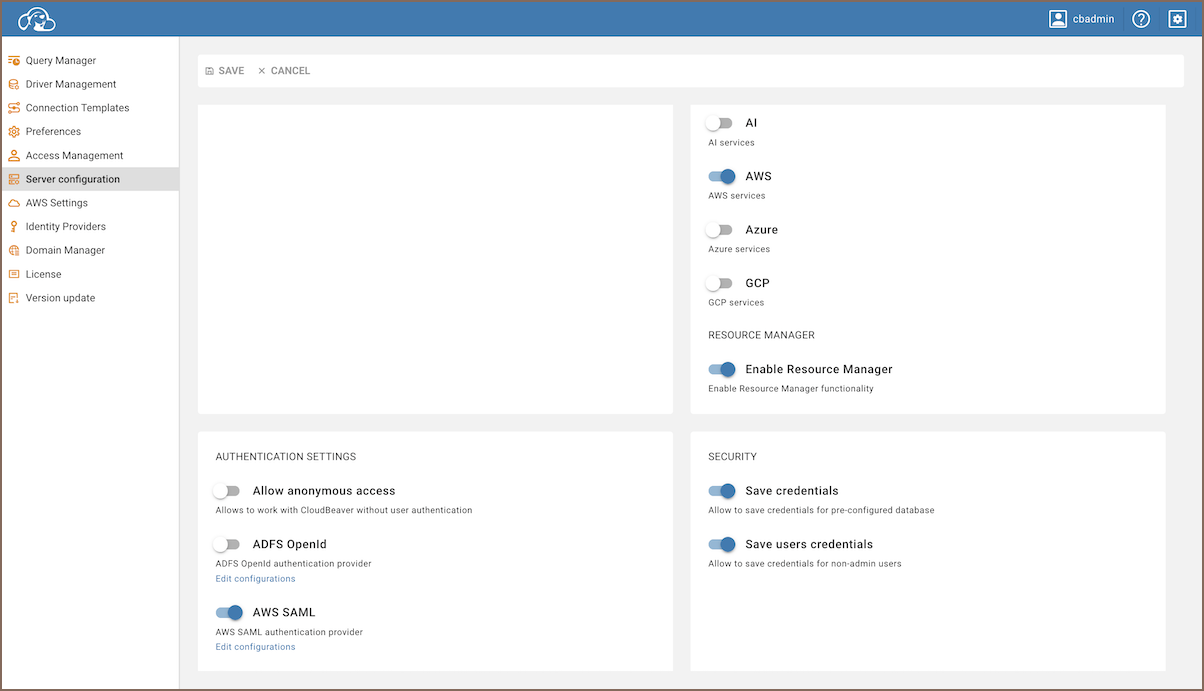
Enable AWS services and AWS SAML provider:
- Navigate to Settings -> Administration -> Server Configuration and select the checkboxes for both AWS and
AWS SAML.
- Navigate to Settings -> Administration -> Server Configuration and select the checkboxes for both AWS and
AWS SAML.
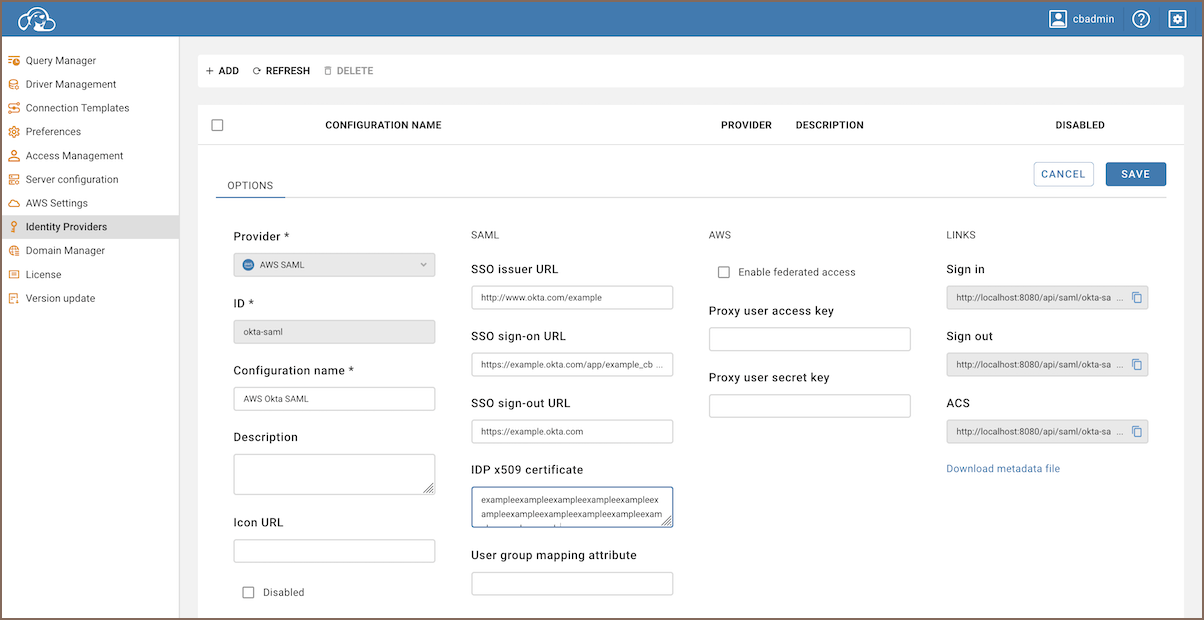
Create a blank Identity Provider:
- Go to Settings -> Administration -> Identity Providers.
- Click on the + Add button to create a draft of a new identity provider.
- Initially, fill in only the necessary fields to generate the Sign-in/Sign-out URLs and ACS links. The remaining fields will be completed later.
- After filling in the fields, click on the Create button to complete the blank identity provider configuration.
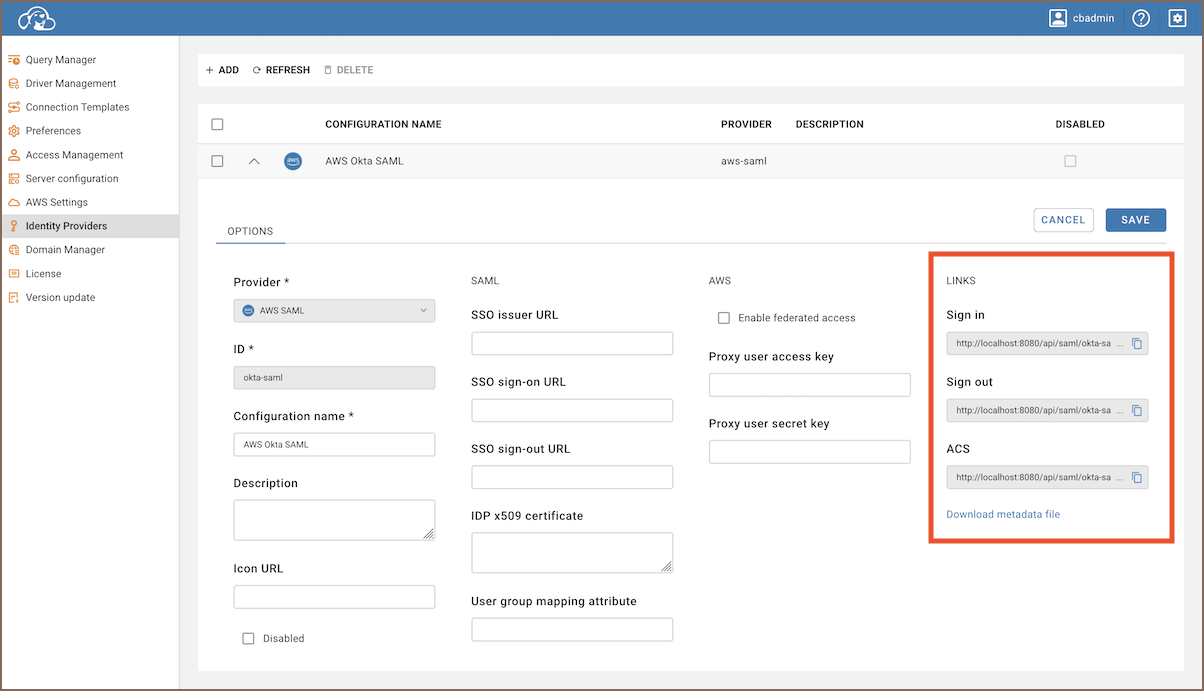
Copy links:
- Enter the newly created identity provider.
- Copy the Sign in, Sign out and the ACS link.
- Also, you need to copy the Entity ID link. To find the Entity ID link, click on the download metadata
file link and copy the
entityIDvalue.
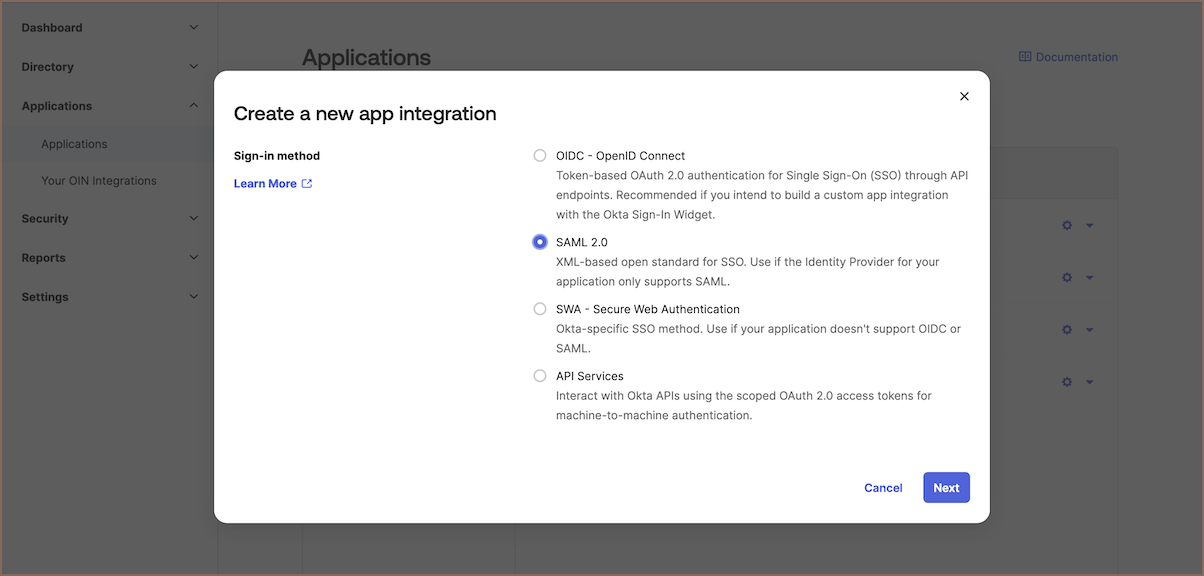
Create SAML 2.0 application in Okta:
- Initiate the process by creating SAML 2.0 application in Okta. For detailed steps, consult the official Okta documentation on application creation.
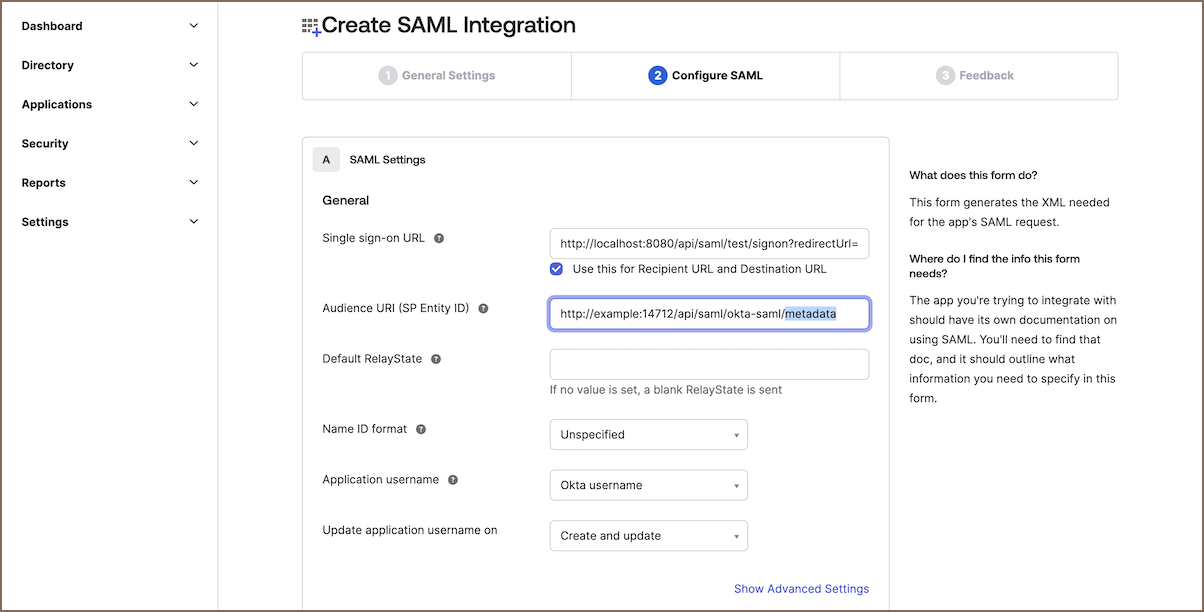
- Under Single Sign-on URL, paste the copied from CloudBeaver application Sign in link.
- In the same section, locate the Audience URI (SP Entity ID). To formulate the Entity ID link, start with
the ACS link from CloudBeaver application. Modify this URL by replacing
the segment that reads
acswithmetadata, and then paste this newly created link into the Audience URI (SP Entity ID) field. - In the same section, locate the Show Advanced Settings button and click to open additional settings.
- Find Other Requestable SSO URIs and click the Add Another + button. Paste the ACS link and enter
0in the Index field. - Insert
http://www.okta.com/${org.externalKey}into the SAML User ID field. This is your provider ID value, which is automatically populated.
- Find Other Requestable SSO URIs and click the Add Another + button. Paste the ACS link and enter
- Click Next and then Finish to finalize these configurations.
Configure SAML settings in CloudBeaver:
- Access Settings -> Administration -> Identity Providers in CloudBeaver.
- Click on the identity provider that was set up for SAML integration.
Retrieve SAML configuration URLs from Okta:
- In Okta, navigate to the Sign On settings of your SAML application.
- Expand the Hide details section to view the necessary URLs.
Enter SAML details into CloudBeaver:
- Copy the SSO sign-on URL, SSO sign-out URL, and the Issuer URL from Okta.
- Paste these URLs into the corresponding fields in CloudBeaver's identity provider settings.
- Upload the IDP x509 certificate, which can be downloaded from Okta, into the respective field in CloudBeaver.
- Complete additional fields
Field Name Description Description (Optional) Provide a brief description of the identity provider. Icon URL (Optional) Enter the URL of an icon to represent this identity provider in CloudBeaver. User group mapping attribute (Optional) Specify the attribute that will be used for mapping user groups between CloudBeaver and the identity provider. - After entering all necessary information, save the settings to finalize the configuration of your SAML identity provider.
Add users to application in Okta:
- In your newly created Okta application, assign people or groups. For detail steps, consult the official Okta documentation on assign applications to users.
Add Identity Provider in AWS IAM:
Add a SAML identity provider in AWS IAM. This allows AWS to authenticate users managed by Okta. For comprehensive instructions, refer to the official AWS documentation on identity providers.

Hint to obtain the Metadata document:
- Navigate to Okta and select your application under Applications.
- Proceed to the Sign On tab, locate the SAML 2.0 section, and click on the Metadata URL.
- Then, paste this URL into a new browser tab to open the XML content. Copy the XML content displayed in your browser into a new file.
- Configure a role for SAML 2.0 federation:
The next step involves configuring an AWS role for SAML. This role will be used to grant permissions based on the authenticated identity from Okta. For a detailed walkthrough, visit the official AWS documentation on creating roles for SAML 2.0 federation.
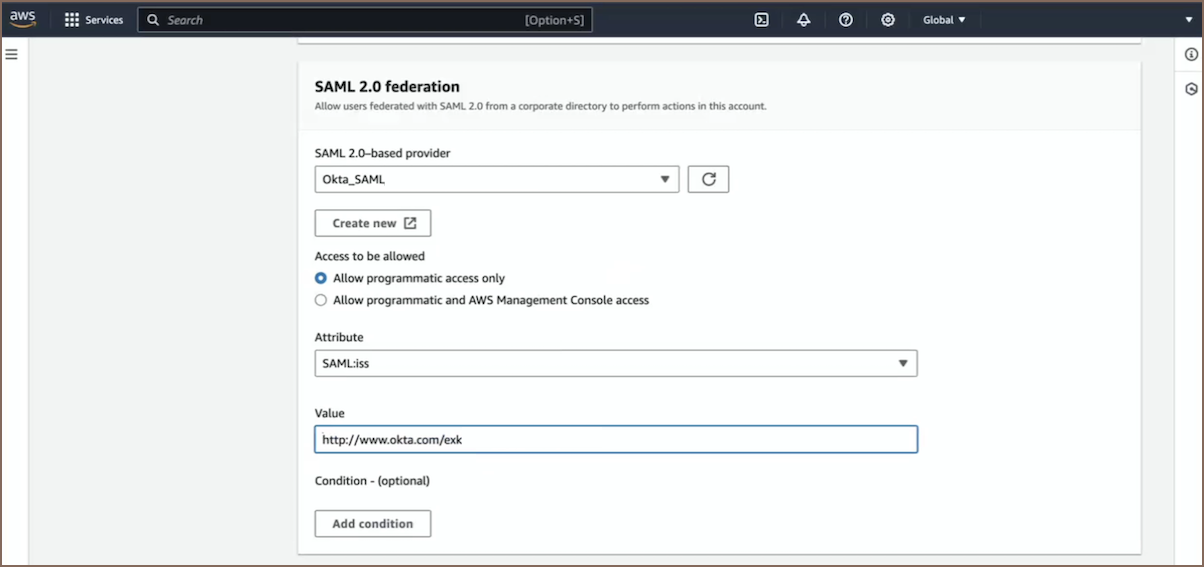
Hints for filling fields on the initial page when creating a role:
- Attribute: You can choose
SAML:iss.- Value: To find Issuer, navigate to Okta and select your application under Applications. Then proceed to the Sign On tab, locate the SAML 2.0 section, and there you will find the Issuer URL to copy.
- Configure SAML attributes in Okta for AWS:
To ensure proper session management and permissions during SAML authentication with AWS, configure the following SAML attributes in Okta:
Steps to Configure SAML Attributes:
- Go to Applications in Okta, select your application, and edit the SAML Settings under General.
- Scroll down to find the SAML Settings section and click Edit to modify the configurations.
- After entering the edit mode, proceed to the Configure SAML section.
- Locate and fill in the Attribute statements (Optional) settings.
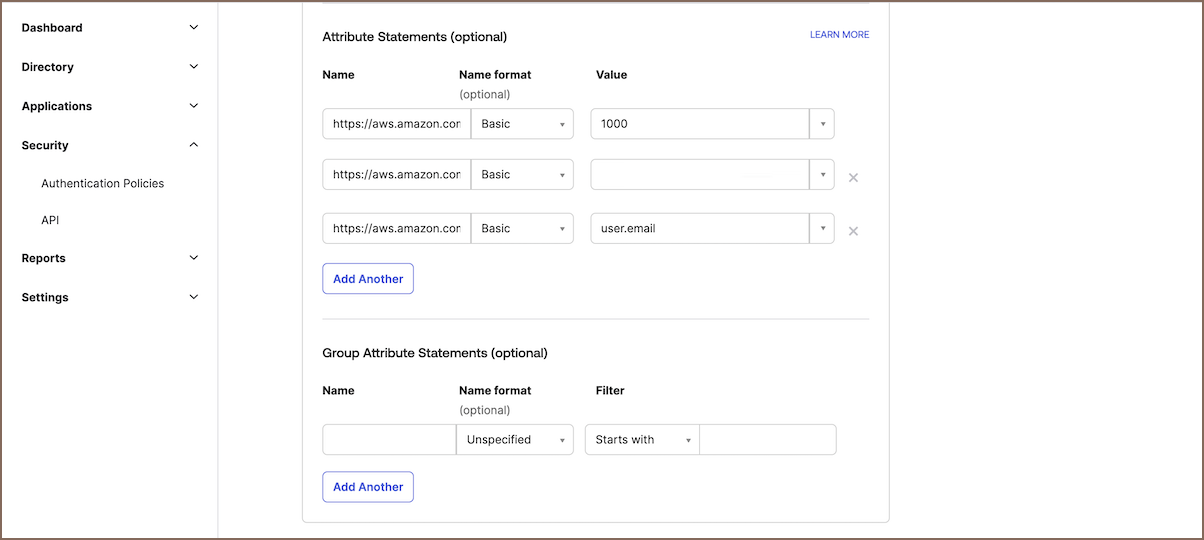
| Attribute Name | Name Format | Value Example | Notes |
|---|---|---|---|
https://aws.amazon.com/SAML/Attributes/SessionDuration | Basic | 3600 | Set in seconds, range: 900 to 43200 seconds. |
https://aws.amazon.com/SAML/Attributes/Role | Basic | arn:aws:iam::123456789012:role/SAMLRole,arn:aws:iam::123456789012:saml-provider/Okta | Format: {roleArn},{identityProviderArn}. |
https://aws.amazon.com/SAML/Attributes/RoleSessionName | Basic | user.email | Use a unique identifier like user.email or user.id. |
Note: In the Value for the Role attribute, ensure the ARNs are correctly copied from AWS IAM. The
roleArnis the ARN for the role created for SAML integration, andidentityProviderArnis the ARN for the identity provider (Okta) configured in AWS IAM.
Set a default role and AWS session lifetime in the SAML configuration for consistent permissions, or customize via attribute mapping for user-specific roles. See documentation for details.
- Now you can log in through the newly created Federated authentication method in CloudBeaver, using the Configuration name you assigned during the setup.
Verify the integration of AWS SAML and Okta
- Once logged in, click on your username in CloudBeaver and navigate to the User Info tab.
- Here, you should see two AUTH tokens. Their presence indicates that the integration of AWS OpenID and Okta has been successfully completed, and CloudBeaver has access to the necessary credentials.
Following successful login, you can access the databases listed in Cloud Explorer that are integrated with your AWS account.
